Disclaimer: This is by no means a complete guide to this setup, but serves only to remind myself of the steps needed for my purposes. If this helps you, great.
Assuming Firepower is already setup and at least 1 Threat Defense node is connected.
SSH Into the FMC to generate the certificate request
openssl -req -newkey rsa:4096 -keyout FMC_KEY.pem -out FMC_CSR.pem
Ensure you remember the passphrase you enter as you’ll need it later
In my case I have a CA configured on Windows Server 2016, so I create a new certificate template as the PXGrid certs require Server & Client authentication
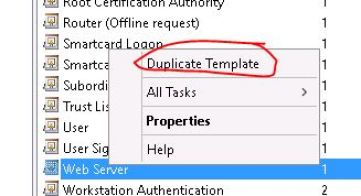
Right click on the Web Server template and make a duplicate
Give it a name and check the publish cert in active directory checkbox
Under Extensions -> Application Policies make sure both Server and Client Authentication are included
Now you have to mark the new template as ready to issue
Using the FMC_CSR.pem file from the FMC, you can just ‘cat’ the file to grab the cert info, then go to your certificate request page:
Click the advanced cert request link
Enter the details from the CSR, select PXGrid template
Now download the cert in Base-64
While you are on the CA, grab a copy of the root cert as the FMC will need that as well. Then go o Objects -> Object Management -> Trusted Certs and toss in the Root CA
Next go to Internal Certs and toss in the new cert you created. You’ll need the FMC_KEY.pem details as well and the passphrase you entered previously
If you haven’t already enabled the PXGrid service in ISE, go ahead and do that now under admin -> Deployment -> Select the node you want it on:
In my case I created a new multi use cert for ISE using that PXGrid template and now using that for all services in ISE
Once you have your Client & Server authentication cert for ISE installed, go ahead and enable ‘Automatically approve new certificate-based accounts’ under PXGrid services -> Settings. This is so ISE automatically accepts new PXGrid connections.
Back at the FMC: System -> Integration -> Identity Sources -> ISE
Enter the details for ISE, and reference the Certs created previously
You should see a success message after clicking on Test. If not, make sure your certs on both sides are good to go, and make sure the PXGrid client isn’t in pending status in ISE
Next, create an intrusion policy on the FMC
Click on Rules
Find the icmp echo rule
Change it to enabled status
Click on the yellow triangle
Commit changes
This is optional
Now create an access policy
Reference the intrusion policy you just created
Under Policies -> Action -> Instances
Create a new remediation instance using the PXGrid module
Give it a name
Add a new remediation type. You can pick mitigate source or destination. In my case the intrusion policy is based on ICMP Echo Reply, so my test host will be the destination of those
Give it a name, and specify the action = Quarantine, Unquarantine, or shutdown
Save
Create a new Correlation Policy
Give it a name an save it
Under Rule Management, create a new one
Give it a name, and specify when an intrusion event occurs against my destination
Save it, and then go back Correlation Policy and edit it. I also enabled the policy at this point, but that should be done later as it’s not completed yet
Add the rule you just created
You should now see the rule under the policy. There is a small icon indicated below. Hard to see, but this is where you specify the action when this rule triggers (quarantine in my case)

Now everything should be in place, just have to make sure the Access Control Policy (which references the intrusion policy) is assigned to your FTD
Now just make sure to deploy all of the changes to the FTD
Now the FMC should tell ISE to quarantine endpoints to trigger the intrusion event. Still have to have ISE do something with that message. Under Operations -> Adaptive Network Control -> Policy List -> Add. Select Quarantine
Now configure a new authorization rule to perform some action when hosts are quarantined. In my case, I toss them into a dead vlan
Now when your host sends a ping to the server specified in the intrusion policy, the ICMP echo reply will:
– Trigger the intrusion policy event
– Triggers the correlation policy rule
– Triggers the quarantine mitigation rule
– ISE then marks the endpoint as quarantined and forces a re-auth
– Endpoint now hits the specified AuthZ Rule toss it into vlan 999
The endpoint will now be stuck in that vlan until someone goes to Ops -> ANC -> Endpoint Assignment and uses the EPS Unquarantine button.
After that, the host should get back online using it’s previous AuthZ rule

















































Be First to Comment